
#CiscoLive
Bart Brinckman
Distinguished Engineer
BREKWN-2037
OpenRoaming under the hood
Jakub Sroga
Network Support Engineer

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Cisco Webex App
Questions?
Use Cisco Webex App to chat
with the speaker after the session
Find this session in the Cisco Live Mobile App
Click “Join the Discussion”
Install the Webex App or go directly to the Webex space
Enter messages/questions in the Webex space
How
Webex spaces will be moderated
by the speaker until June 7, 2024.
1
2
3
4
https://ciscolive.ciscoevents.com/
ciscolivebot/#BREKWN-2037
Enter your personal notes here
2
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco PublicBRKEWN-2037

Agenda
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
• What is it and why would I
use it?
• How it works under the hood
• Your own Identity: SDK and
Web-based provisioning
• Configuration and Live Demo
with Meraki
• Conclusion
BRKEWN-2037
3

What
is OpenRoaming?
Why would I use it?
We start with…

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
5
BRKEWN-2037
Reality today

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
6
BRKEWN-2037
Reality today
password:
Username: g00dLuck
Password: zk1sowcaStF98LOZo2x

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
7
BRKEWN-2037
7
BRKEWN-2037
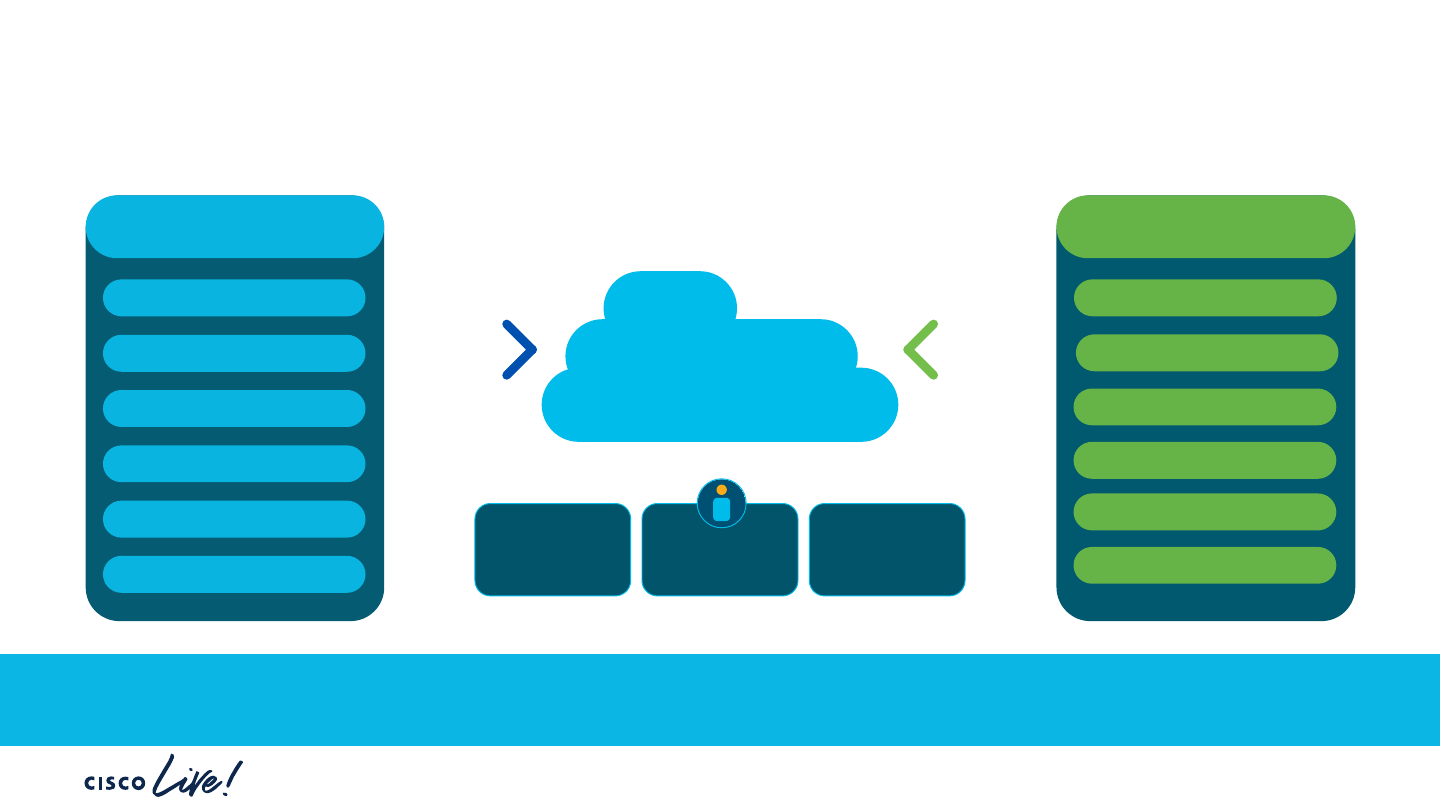
Our Goal: Intelligent Multi-Access
Seamless Handover
Roaming between Wi-Fi (private)
and cellular (public)
Seamless Interworking
Policy-based path selection for
Loosely coupled Access Networks
Frictionless Onboarding
OpenRoaming
(assure access to all available paths)
Access providers
Public
Ent. Guest
Home Driving Corporate
office
Customer
call in the car
Visit to the secure
warehouse
Coffee shop Hotel
Identity providers
Service-based
Football
match
WiFi6
5G
Converged Access for People and Things
To use all wireless stacks better, we need…
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
8
BRKEWN-2037
OpenRoaming: Opening the Wi-Fi Ecosystem to
new experiences & business models
• Leverage Identity Federation to scale and facilitate relationships
OpenRoaming is a federation of identity & access providers
to enable seamless roaming & onboarding
Identity
Federation
Join
Join
Guest/Thing
on
Wi-Fi
Legal
Framework
Discovery,
Policy,
Security &
Privacy
Access providers Identity providers
Venue / Loyalty
MSO
Web/Cloud
Enterprise
Enterprise
Healthcare
Retail
Hospitality
Education
Smart City
MNO
Device

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
9
BRKEWN-2037
Which ID’s are available?
9:41 AM
100
%
Open Roaming
To enjoy seamless and secure WiFi,
please choose an account for activation
Continue with Apple
Continue with Google
OpenRoaming
Cloud ID
Device
Embedded
LoyaltyEnterprise
Service
Provider

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
10
Use case: Seamless onboarding use case
Use Case:
Get users seamlessly and securely connected to a venue’s
Wi-Fi network
Value proposition:
User
Better user experience, device is on the internet and ready to go
Enhanced Security & Privacy vs portal-based solution
Venue
Improved customer experience & satisfaction
Reduced IT and non-IT staff burden: Wi-Fi as easy as power
Secure and private: lower exposure to malicious actors
Analytics venue flow and density analytics
Who should run it?
• Public areas: Municipal Wi-Fi, libraries, public buildings
• Healthcare: Hospitals and care centers
• Transportation: Airports and train stations
• Retail: Shopping malls, big box stores
• Hospitality: Hotels and event venues
Via Wi-Fi Picker Via Notification Bar

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Use case: Service provider indoor coverage
Use Case:
Improve bad SP indoor coverage at a fraction of the cost of
DAS (Digital Antenna Systems)
Value proposition:
User
Good indoor voice and data
Venue
Improved customer experience & satisfaction
Reduced IT and non-IT staff burden: Wi-Fi as easy as power
Lower cost alternative than DAS or in combination with DAS for
lower-cost capacity
Own the Analytics: venue flow and density analytics
Who should run it?
• Public indoor areas: libraries, public buildings
• Healthcare: Hospitals and care centers
• Transportation: Airports and train stations
• Retail: Shopping malls, big box stores, supermarkets
• Hospitality: Hotels and event venues
Cost-comparison to DAS
SP1 on DAS* SP2 on Wi-Fi*
BRKEWN-2037
11

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
12
Use case: Smart contextual loyalty experiences
Use Case:
Connect loyalty users and visitors seamlessly, get person-
based insights, and communicate with visitor in real-time
Value proposition:
User
Better user experience, device is on the internet and ready to go
Able to communicate with the venue in real-time
Venue
Improved customer experience & satisfaction
Reduced IT and non-IT staff burden: Wi-Fi as easy as power
Better persona-based Analytics
Real-time location-based notifications
Who should run it?
• Retail: Shopping malls, big box stores, grocery stores
with loyalty programs
• Hospitality: Hotels with loyalty programs, events with
event/fan apps, …
• Healthcare: Hospitals with patient apps

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
13
Use Case summary
Smart, Contextual Loyalty
Experiences
• iOS & Android: DNA
Spaces SDK
• Web-based APIs for Web
and Portal
Seamless, Secure
Onboarding & User
Insights
• OpenRoaming Mobile App
• Devices with Native
Support
• Publicly available IDPs
Enhance Indoor Coverage
• Service Provider (SP)
Offload to Wi-Fi
• Devices with Native
Support
• Publicly available IDPs
DNA Spaces SEE DNA Spaces ACT DNA Spaces EXTEND

How it works
under the hood
What we are all here for…

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
15
BRKEWN-2037
15
BRKEWN-2037
The basic idea: Leverage and modernize roaming
Identity providers
Venue / Loyalty
MNO
MSO
Web
Enterprise
1
Pre-association policy exchange: Market
reality drives to leverage widely adopted
technology and improve over time
PassPoint
Phase 1: leverage what is supported
• Repurpose home/visited concept
so signal IDP prioritization
• leverage 5 Byte RCOI field to
signal policy
Phase 2: Improve the standard
• Update standard attributes to
support policy exchange
2
Scalable and secure roaming
solution that is open to any IDP and
scales to millions of participants
SP SP
Hub
SP
SP
SP
SP
SP
SP
Current methodologies scale to 100’s of participants
Bilateral agreements
Roaming HUB’s
Identity federation scales to millions of participants:

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
16
OpenRoaming: Building blocks
A
c
c
e
s
s
P
r
o
v
i
d
e
r
S
i
g
n
u
p
I
d
P
S
i
g
n
u
p
Identity
Provider
Identity
Provider
open- roaming
Identity
Federation
Authentication & Accounting
Service discovery Service Advertisement
Wi- Fi
Access
Network
Identity
Provider
1
Identity Federation: PKI-based trust model and
legal framework
3
Dynamic policy at the edge enables real-time
ad-hoc roaming agreements
2
Federation that dynamically discovers peers &
services and allows for secure direct peering
Policy
Policy
4
Secure Authentication and accounting
over TLS
5
Proxy services can connect cloud-based
identities or offer value-added services
(e.g. settlement)
Proxy
Service
OpenRoaming
Identity
Federation

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
17
Federation Architecture
PKI Framework Legal Framework
End user Terms
of Service
Identity Provider
agreement
Access Network
agreement
WBA
ROOT CA
CISCO
SIGNING I-CA
GOOGLE
SIGNING I-CA
WBA
SIGNING I-CA
KYRIO
SIGNING I-CA
WBA
POLICY CA
governs acceptable
use and privacy
Govern roaming
Governs service and
acceptable use
Cisco
customers &
partners
Google
customers &
partners
WBA members Anyone (paid)

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
18
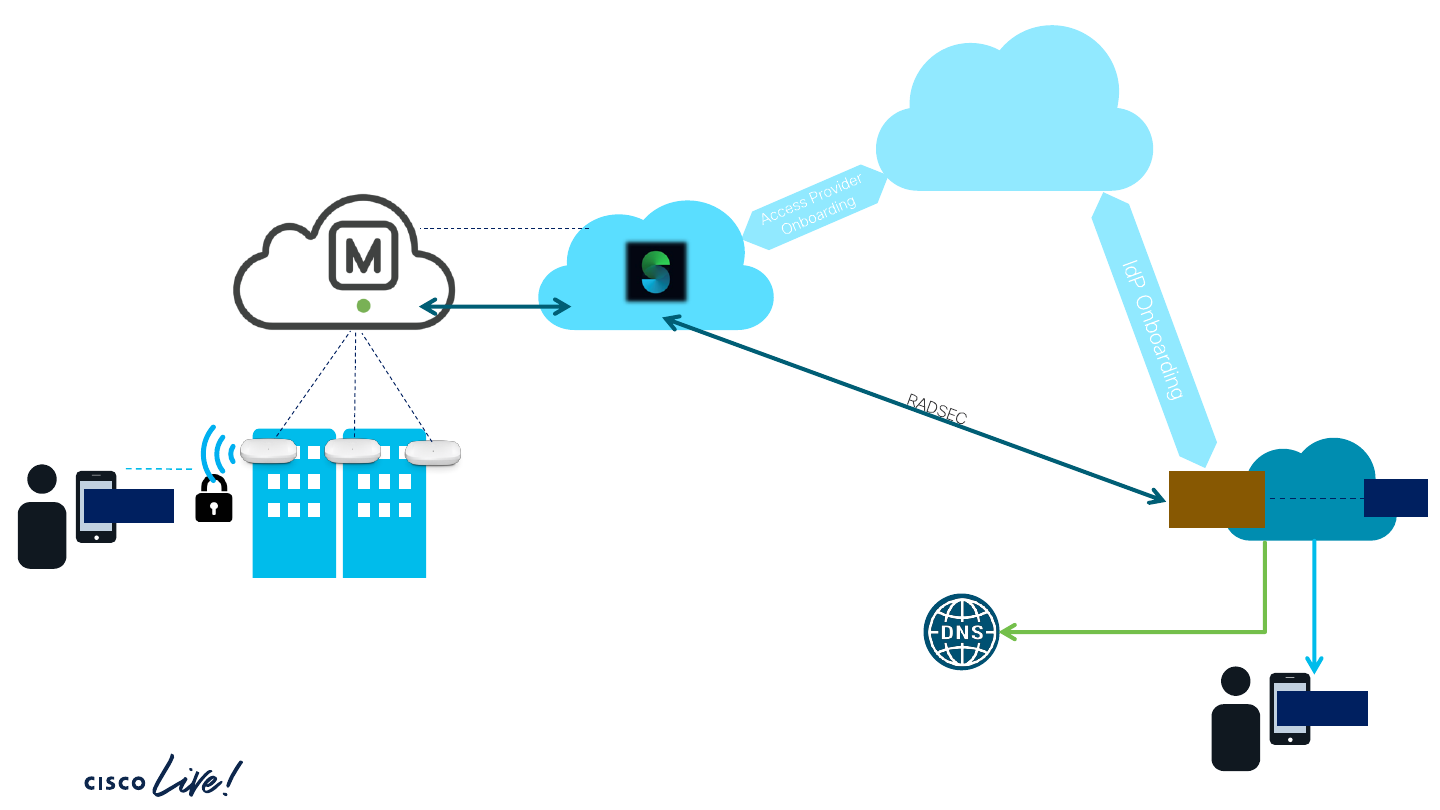
AireOS/Catalyst Architecture
OpenRoaming
Identity Federation
RADSEC
IDP
Hotspot
connector
RADSEC
PROXY
(or AAA)
AAA
Credential
Certificate Authority &
Revocation service
Sign-up/Manage
Credential
Controller
RADIUS
RADIUS
• OpenRoaming.org PKI management
• DNS-based IDP discovery
• TLS tunnel management
• RADIUS-RADSEC proxy
• RADIUS attribute adaptation
Management
Websocket
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
19
Meraki Architecture
OpenRoaming
Identity Federation
IDP
RADSEC
PROXY
(or AAA)
AAA
Credential
Sign-up/Manage
Credential
RADIUS
RADIUS over
Secure Meraki Tunnel
Meraki API provisioning
(Certs, SSID)
RADSEC

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
20

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
21
Wi-Fi
Access
Network
Complete onboarding flow
Identity
Provider
Authentication, Policy, Accounting
ANQP +
EAP-based
User
Authentication
TLS based
encryption
Enterprise
based security
IDP controls
privacy
IDP Discovery
Configure DNS
OpenRoaming
Identity Federation
Device
Automatic
SSID discovery
using PassPoint

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
22
Wi-Fi
Access
Network
Onboarding flow – SSID discovery
Identity
Provider
ANQP +
EAP-based
User
Authentication
Enterprise
based security
IDP controls
privacy
Configure DNS
OpenRoaming
Identity Federation
Device
Automatic
SSID discovery
using PassPoint

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
23
SSID discovery and selection using 802.11u
Device AP/WLC
Device roams into
wireless coverage
Device selects profile
802.11u Scan Request
802.11u Scan Report
802.11u GAS request (AQNP Query)
802.11u GAS response (AQNP Resp)
Associate
1
AP Beacon or Probe response info
RCOIs:
004096
5a03ba0000

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
OpenRoaming RCOI
Description WBA Roaming OI Cisco Roaming OI
All
5A03BA0000
004096
All with real
-ID only
5A03BA1000
00500B
All paid
BAA2D00000
00500F
Device Manufacturer
5A03BA0A00
00502A
Device Manufacturer real
-ID
5A03BA1A00
0050A7
Cloud ID
5A03BA0200
005014
Cloud ID real
-ID
5A03BA1200
0050BD
Enterprise ID
5A03BA0300
00503E
Enterprise ID real ID
5A03BA1300
0050D1
Enterprise Customer
program ID
Not defined
005050
Enterprise Customer program real
ID
Not defined
0050E2
Loyalty Retail
5A03BA0B00
005053
Loyalty Retail real ID
5A03BA1B00
0050F0
Loyalty Hospitality
5A03BA0600
005054
Loyalty Hospitality real ID
5A03BA1600
00562B
SP free Bronze Qos
5A03BA0100
005073
SP free Bronze Qos Real ID
5A03BA1100
0057D2
SP paid Bronze QoS
BAA2D00100
Not defined
SP paid Bronze QoS real ID
BAA2D01100
Not defined
SP paid Silver QoS
BAA2D02100
Not defined
SP paid Silver QoS real ID
BAA2D03100
Not defined
SP paid Gold QoS
BAA2D04100
Not defined
SP paid Gold QoS real ID
BAA2D05100
Not defined
Roaming Consortium
Organization Identifier (RCOI) :
• Allow all: Accepts users from any
identity provider (IDP), with any
privacy policy.
• Real ID: Accepts users from any
IDP, but only with a privacy policy
that shares real identity (anonymous
not accepted).
• Custom: Accepts users of select
identity types and privacy policies
associated with the identity types.
New ID Types in OR
-Std:
WBA Roaming OI Cisco Roaming OI
Government ID free
5A03BA0400
Not defined
Automotive ID free
5A03BA0500
Not defined
Automotive Paid
BAA2D00500
Not defined
Education/Research ID free
5A03BA0800
Not defined
Cable ID free
5A03BA0900
Not defined

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
25
BRKEWN-2037
802.11u GAS Initial Request (STA) and Response (AP)
AP response .11u and ANQP
Device AP/WLC
Device roams into
wireless coverage
Device selects profile
802.11u Scan Request
802.11u Scan Report
802.11u GAS request (AQNP Query)
802.11u GAS response (AQNP Resp)
Associate
2
STA request additional information .11u and ANQP
NAI Realm: openroaming.org
Domain: preferreddomain.com

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
26
Wi-Fi
Access
Network
Onboarding flow – IDP discovery
Identity
Provider
ANQP +
EAP-based
User
Authentication
Enterprise
based security
IDP controls
privacy
IDP Discovery
Configure DNS
OpenRoaming
Identity Federation
Device
Automatic
SSID discovery
using PassPoint

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
27
IDP Discovery Call Flow (RFC-7585)
Access Provider
Identity Provider
IDP
DNS
Connector
AP/WLCDevice
EAPOL Start
Device roams into wireless
coverage
EAP Request Identity
EAP Response Identity
RADIUS Access Request
(User-Name:
NAPTR Query w/ Realm
(domain.com)
NAPTR Response (protocol +
SRV record)
SRV Query w/ SRV Record
A Query with FQDN record
A Response (AAA IP Address)
SRV Response (FQDN + port
number)
sdk.openroaming.net
dig -t naptr sdk.openroaming.net
sdk.openroaming.net. 300 IN NAPTR 50 50 "s"
"aaa+auth:radius.tls.tcp" "" _radiustls._tcp.sdk.openroaming.net.
dig -t srv _radiustls._tcp.sdk.openroaming.net
_radiustls._tcp.sdk.openroaming.net. 300 IN SRV 0 10 2083
idp.openroaming.net.
dig -t a idp.openroaming.net
idp.openroaming.net. 300 IN A 3.208.239.144
AT&T PLMN 410
dig -t naptr wlan.mnc410.mcc310.pub.3gppnetwork.org
wlan.mnc410.mcc310.pub.3gppnetwork.org. 3600 IN NAPTR 50 50
"s" "aaa+auth:radius.tls.tcp" "" _radiustls._tcp.3af521.net.
dig -t srv _radiustls._tcp.3af521.net.
_radiustls._tcp.3af521.net. 300 IN SRV 0 10 2083 idp.3af521.net.
dig -t a idp.3af521.net
idp.3af521.net. 300 IN CNAME public-radius-
service.production.radius.one.singledigits.com.
public-radius-service.production.radius.one.singledigits.com. 60 IN
CNAME a8f7a7d1bd6e54b4babbed926a990720-
b4bc5d7f98840512.elb.us-east-1.amazonaws.com.
a8f7a7d1bd6e54b4babbed926a990720-b4bc5d7f98840512.elb.us-
east-1.amazonaws.com. 60 IN A 54.146.180.226
a8f7a7d1bd6e54b4babbed926a990720-b4bc5d7f98840512.elb.us-
east-1.amazonaws.com. 60 IN A 54.83.92.42

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
28
Wi-Fi
Access
Network
Onboarding flow – TLS Tunnel Setup
Identity
Provider
ANQP +
EAP-based
User
Authentication
TLS based
encryption
Enterprise
based security
IDP controls
privacy
IDP Discovery
Configure DNS
OpenRoaming
Identity Federation
Device
Automatic
SSID discovery
using PassPoint

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
29
TLS Tunnel Setup Between Access Provider and IDP
Access Provider
Identity Provider
IDP
AAA
TLS Certificate ClientKeyExchange, Certificate
Verify, Change Cipher Spec, Finished
TCP SYN
TCP SYN ACK
TLS Server Hello, Server Certificate,
Certificate Request, ServerHelloDone
TLS Client Hello
TLS Change Cipher Spec, Finished
Connect
or
Connector verifies
Server certificate,
certificate chain,
validity, revocation, CN
vs AAA FQDN,
SubjectAltName vs
Realm
IDP AAA verifies Client
Certificate: certificate
chain, validity,
revocation, UID vs
Operator-ID (optional)
openssl s_client -connect idp.openroaming.net:2083 check SSL connection
CONNECTED(00000005)
depth=3 C = US, ST = California, L = San Jose, O = "Cisco Systems, Inc.", OU = Openroaming, CN = openroaming.org, emailAddress = enb-
devops@cisco.com
verify error:num=19:self signed certificate in certificate chain
verify return:0
140704668922688:error:1401E412:SSL routines:CONNECT_CR_FINISHED:sslv3 alert bad certificate:/AppleInternal/Library/BuildRoots/97f6331a-
ba75-11ed-a4bc-863efbbaf80d/Library/Caches/com.apple.xbs/Sources/libressl/libressl-3.3/ssl/ssl_pkt.c:1008:SSL alert number 42
---
Certificate chain
0 s:/C=US/ST=CA/O=Cisco/CN=idp.openroaming.net
i:/C=US/O=Cisco Systems Inc./OU=DNASpaces/ST=California/CN=cisco.openroaming.org/L=San Jose
1 s:/C=US/O=Cisco Systems Inc./OU=DNASpaces/ST=California/CN=cisco.openroaming.org/L=San Jose
i:/C=SG/ST=Singapore/L=Singapore/O=Wireless Broadband Alliance/OU=WBA/CN=openroaming.org/dnQualifier=WBA WRIX ECC Policy
Intermediate CA-01
2 s:/C=SG/ST=Singapore/L=Singapore/O=Wireless Broadband Alliance/OU=WBA/CN=openroaming.org/dnQualifier=WBA WRIX ECC Policy
Intermediate CA-01
i:/C=US/ST=California/L=San Jose/O=Cisco Systems, Inc./OU=Openroaming/CN=openroaming.org/emailAddress[email protected]
3 s:/C=US/ST=California/L=San Jose/O=Cisco Systems, Inc./OU=Openroaming/CN=openroaming.org/[email protected]m
i:/C=US/ST=California/L=San Jose/O=Cisco Systems, Inc./OU=Openroaming/CN=openroaming.org/emailAddress[email protected]
---
Server certificate
subject=/C=US/ST=CA/O=Cisco/CN=idp.openroaming.net
issuer=/C=US/O=Cisco Systems Inc./OU=DNASpaces/ST=California/CN=cisco.openroaming.org/L=San Jose
---
Acceptable client certificate CA names
/C=US/ST=California/L=San Jose/O=Cisco Systems, Inc./OU=Openroaming/CN=openroaming.org/emailAddress=enb-devops@cisco.com
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 6164 bytes and written 138 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 9965F3B5DF5C740E7FEF85D01DB29FA2688237B007C46EDE537DF169031276B7
Session-ID-ctx:
Master-Key: 81A4848377685711A43018559E14CA4842A82FDC27017D1CCD6F32894DC32148219A91C5ED7F4E4865734CBF50417E6D
Start Time: 1683543981
Timeout : 7200 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
---
openssl s_client -connect idp.openroaming.net:2083 -showcertsshow certificate chain(s)
openssl s_client -connect idp.openroaming.net:2083 -msg show all messages

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
30
Wi-Fi
Access
Network
Onboarding flow – packet flow inside TLS Tunnel
Identity
Provider
Authentication, Policy, Accounting
ANQP +
EAP-based
User
Authentication
TLS based
encryption
Enterprise
based security
IDP controls
privacy
IDP Discovery
Configure DNS
OpenRoaming
Identity Federation
Device
Automatic
SSID discovery
using PassPoint

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
31
BRKEWN-2037
RADSEC EAP Authentication: EAP-TTLS
Access
Provider
Identity
Provider
IDP DNSDevice AP/WLC Connector
Device roams into
wireless coverage
IDP AAA
Device selects profile
RADIUS Access Request
(User-Name: [email protected])
IDP Discovery (1)
TLS Tunnel Setup (2)
RADSEC Access Request (User-Name: [email protected])
RADSEC Challenge request (request TLS exchange)
RADIUS Challenge request (request
TLS exchange)
RADIUS Challenge response (response
TLS exchange)
RADSEC Challenge response (response TLS exchange)
RADSEC Challenge request (request TLS inner identity)
RADIUS Challenge request (request
TLS inner identity)
RADIUS Challenge response (TLS inner
identity)
RADSEC Challenge response (response TLS exchange)
RADSEC Access Accept (unique identifier)
RADIUS Access Accept (unique
identifier)
802.11u Scan Request
802.11u Scan Report
802.11u GAS request (AQNP Query)
802.11u GAS response (AQNP Resp)
Associate
EAP Request Identity
EAP Response Identity
EAP Request TLS exchange
EAP Response TLS
exchange
EAP Request TLS inner identity
EAP Response TLS inner
identity
EAP Access Accept (unique
identifier)

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
32
RADSEC EAP Authentication: EAP-TTLS (detailed)
AP/WLC Radius Access-Request to Spaces Connector:
=> Anonymous User Name
=> NAS is the AP/WLC
=> AP Radio MAC : SSID
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
33
BRKEWN-2037
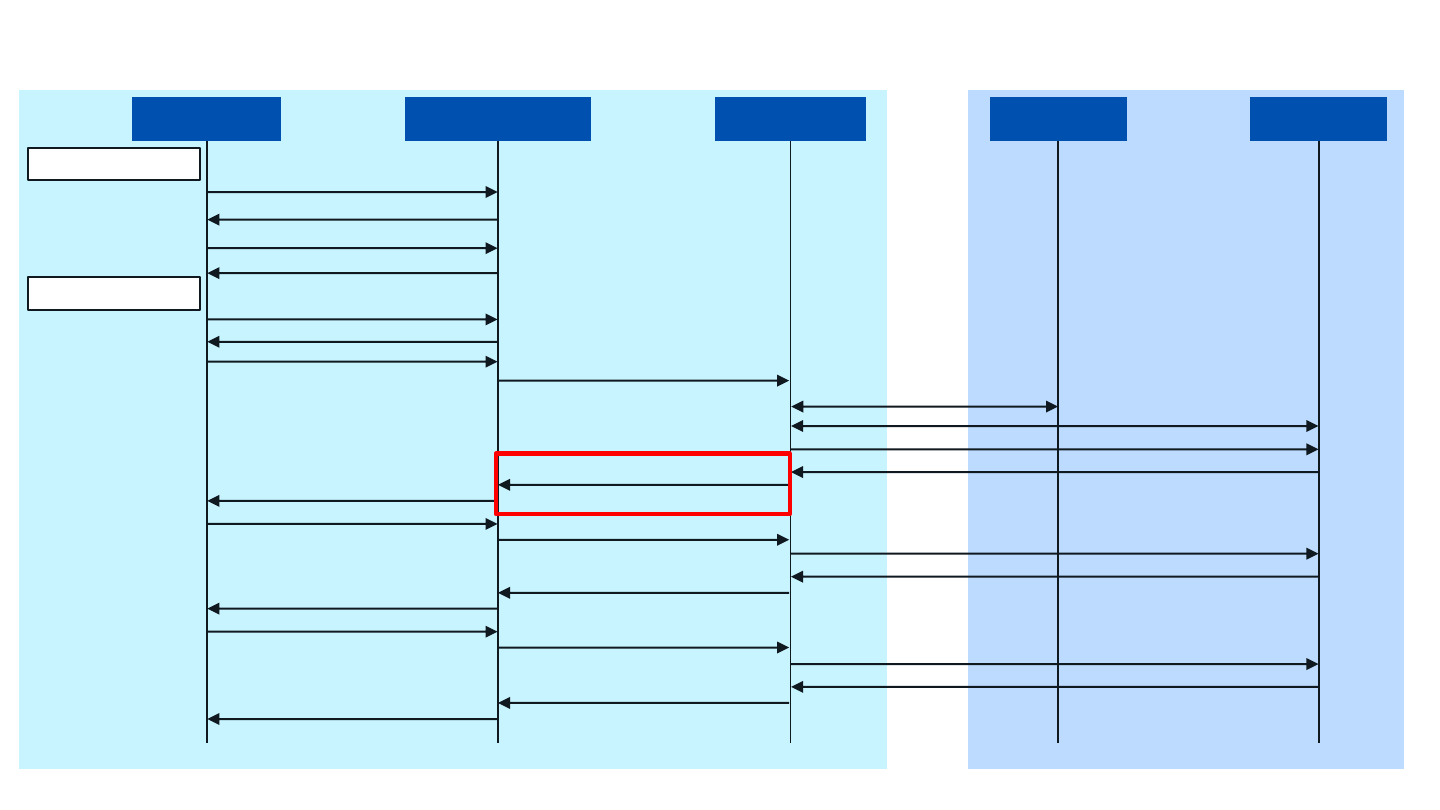
RADSEC EAP Authentication: EAP-TTLS
Access
Provider
Identity
Provider
IDP DNSDevice AP/WLC Connector
Device roams into
wireless coverage
IDP AAA
Device selects profile
RADIUS Access Request
(User-Name: [email protected])
IDP Discovery (1)
TLS Tunnel Setup (2)
RADSEC Access Request (User-Name: [email protected])
RADSEC Challenge request (request TLS exchange)
RADIUS Challenge request (request
TLS exchange)
RADIUS Challenge response (response
TLS exchange)
RADSEC Challenge response (response TLS exchange)
RADSEC Challenge request (request TLS inner identity)
RADIUS Challenge request (request
TLS inner identity)
RADIUS Challenge response (TLS inner
identity)
RADSEC Challenge response (response TLS exchange)
RADSEC Access Accept (unique identifier)
RADIUS Access Accept (unique
identifier)
802.11u Scan Request
802.11u Scan Report
802.11u GAS request (AQNP Query)
802.11u GAS response (AQNP Resp)
Associate
EAP Request Identity
EAP Response Identity
EAP Request TLS exchange
EAP Response TLS
exchange
EAP Request TLS inner identity
EAP Response TLS inner
identity
EAP Access Accept (unique
identifier)

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
34
RADSEC EAP Authentication: EAP-TTLS (detailed)
Spaces Connector Radius Access-Challenge to AP/WLC
=> EAP Type TTLS

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
35
BRKEWN-2037
RADSEC EAP Authentication: EAP-TTLS
Access
Provider
Identity
Provider
IDP DNSDevice AP/WLC Connector
Device roams into
wireless coverage
IDP AAA
Device selects profile
RADIUS Access Request
(User-Name: [email protected])
IDP Discovery (1)
TLS Tunnel Setup (2)
RADSEC Access Request (User-Name: [email protected])
RADSEC Challenge request (request TLS exchange)
RADIUS Challenge request (request
TLS exchange)
RADIUS Challenge response (response
TLS exchange)
RADSEC Challenge response (response TLS exchange)
RADSEC Challenge request (request TLS inner identity)
RADIUS Challenge request (request
TLS inner identity)
RADIUS Challenge response (TLS inner
identity)
RADSEC Challenge response (response TLS exchange)
RADSEC Access Accept (unique identifier)
RADIUS Access Accept (unique
identifier)
802.11u Scan Request
802.11u Scan Report
802.11u GAS request (AQNP Query)
802.11u GAS response (AQNP Resp)
Associate
EAP Request Identity
EAP Response Identity
EAP Request TLS exchange
EAP Response TLS
exchange
EAP Request TLS inner identity
EAP Response TLS inner
identity
EAP Access Accept (unique
identifier)

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
36
RADSEC EAP Authentication: EAP-TTLS (detailed)
Spaces Connector Radius Access-Accept to AP/WLC:
=> Inner Identity – user shared the email
=> Unique Identifier

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
37
OpenRoaming – Privacy Built-in
1
Authentication is private
Secure and private authentication between user’s device and IDP
IDP
3
IDP shares identities on the user’s behalf
IDP manages identity and privacy for the user
2
User and device are identified in context
Identified with persistent Device ID and User ID with IDP context
IDP shares (anonymized) data in the secured path
Device ID
User ID
erj50349jf35g65@cisco.com
4
Privacy with user consent
User controls privacy, identifiers are always persistent
Share my email
Hide my email
ekg40g9vee93@cisco.com
IDP
Wi-Fi
Access
Network

Your own Identity:
SDK and Web-
based
provisioning

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Spaces SDK
Main SDK methods
39
BRKEWN-2037
Initialization
• The app registers
with the Cisco DNA
Spaces account
using the account
API key.
User Identity
Association
• User logs onto the
app using either:
o IDP supported by
DNA Spaces
Backend
o Enterprise or
Loyalty ID
• User sets their
privacy preference
Install
OpenRoaming
Profile
• The profile
associated with the
user identity is
installed on their
device
• Allows devices to
automatically log into
OpenRoaming
networks
Enable Push
Notifications
• Allows for DNA
Spaces backend to
send notifications to
user devices
Location
Information
• The app will report
back the current
location of the
device back to DNA
Spaces
• The location can be
used for use cases
like wayfinding or
targeted
engagements

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
40
SDK for iOS & Android
App
SDK
App Identity
Backend
IDPaaS
API’s
Profile
Management
OpenID Connect
SAML
Provisioning
Authentication
https://developer.cisco.com/dna-spaces-sdk/

Configuration
and Live Demo

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
42
BRKEWN-2037
Create an OpenRoaming Profile
Enable Hotspot Connector
Select Catalyst controller
Configure the OpenRoaming SSID
Spaces OpenRoaming Configuration Steps
1
2
3
4
Create an OpenRoaming Profile
Enable Meraki API
Select Meraki network
Configure the OpenRoaming SSID
1
2
3
4
Demo Time!

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
43
BRKEWN-2037
Prerequisites

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
44
BRKEWN-2037
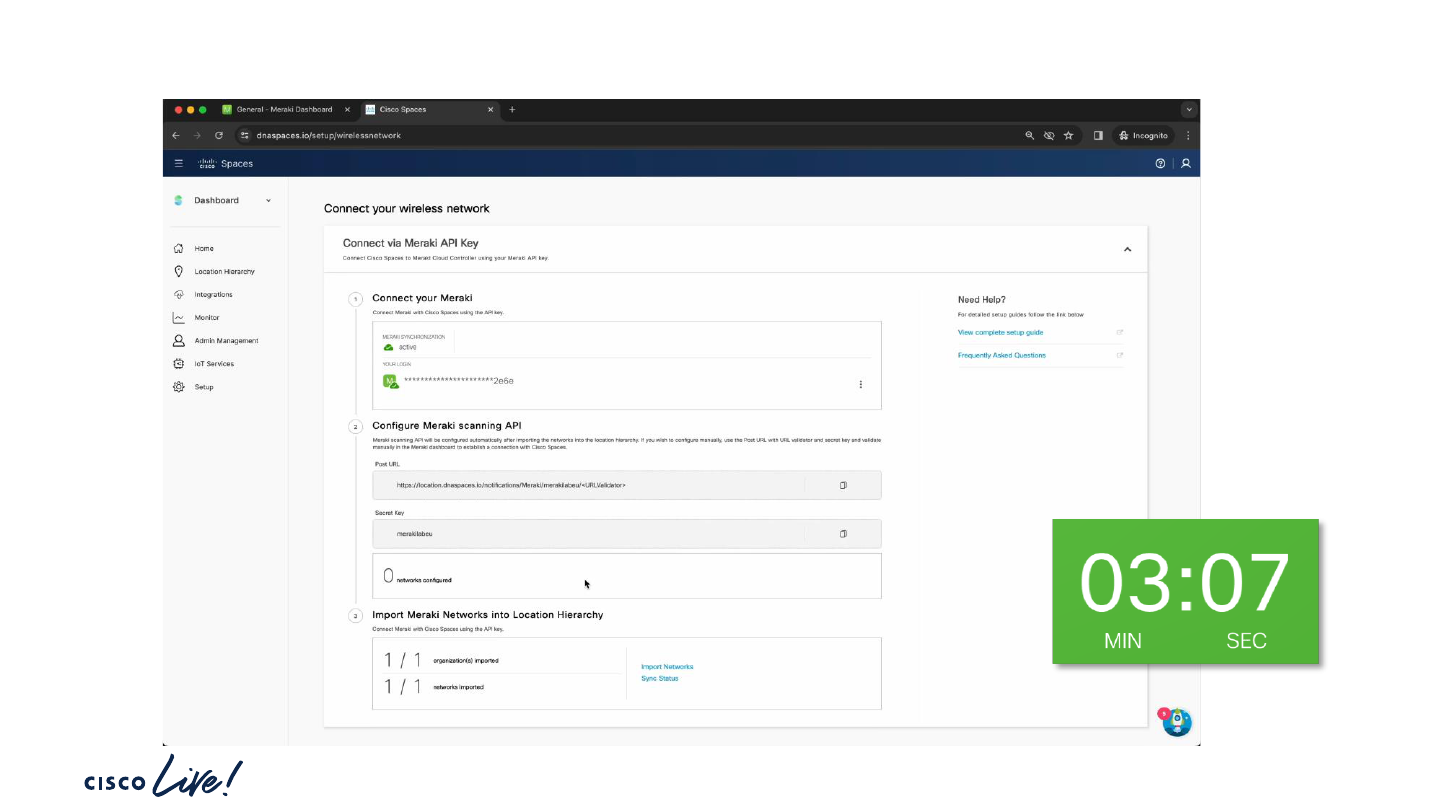
Connect Meraki Dashboard with Cisco Spaces
© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
45
BRKEWN-2037
Configuration

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
46
BRKEWN-2037
Let’s summarize it
Prerequisites Linking both platforms
Configuration

Conclusion

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
48
BRKEWN-2037
Conclusion: Try OpenRoaming!
• If you do not have a Spaces account, get a free trial:
https://spaces.cisco.com/start-for-free/
• If you do not have a Meraki account, and device, get
free trial:
https://meraki.cisco.com/form/trial/
• If you have a spaces account, log in and activate
OpenRoaming:
https://ciscospaces.io/login
9:41 AM
100
%
Open Roaming
To enjoy seamless and secure WiFi,
please choose an account for activation
Continue with Apple
Continue with Google
OpenRoaming
Try it out!

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
BRKEWN-2037
49
References to learn more about OpenRoaming
• Catalyst 9800 WLC Config Guide – OpenRoaming:
• https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-11/config-
guide/b_wl_17_eleven_cg/m_hotspot-2.html
• Meraki OpenRoaming integration with Cisco Spaces Documentation:
• https://documentation.meraki.com/MR/Other_Topics/OpenRoaming_integration_with_Cisco_Spaces
• Cisco Spaces OpenRoaming Configuration Guide:
• https://www.cisco.com/c/en/us/td/docs/wireless/spaces/openroaming/b-spaces-or-cg/m-config-or.html
• Cisco Spaces Connector 3.0 Config Guide:
• https://www.cisco.com/c/en/us/td/docs/wireless/spaces/connector/config/b_connector_30.html
• How to configure OpenRoaming at C9800 Video: https://youtu.be/XsD6e6F6u4k
• Cisco Spaces SDK: https://developer.cisco.com/dna-spaces-sdk/
• WBA OpenRoaming: https://wballiance.com/openroaming/

Q&A

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
Continue
your education
• Visit the Cisco Showcase
for related demos
• Book your one-on-one
Meet the Engineer meeting
• Attend the interactive education
with DevNet, Capture the Flag,
and Walk-in Labs
• Visit the On-Demand Library
for more sessions at
www.CiscoLive.com/on-demand
Contact us at:
51
BRKEWN-2037

© 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
#CiscoLive
Complete Your Session Evaluations
52
BRKEWN-2037
Complete a minimum of 4 session surveys and the Overall Event Survey to be
entered in a drawing to win 1 of 5 full conference passes to Cisco Live 2025.
Earn 100 points per survey completed and compete on the Cisco Live
Challenge leaderboard.
Level up and earn exclusive prizes!
Complete your surveys in the Cisco Live mobile app.

Thank you
#CiscoLive
